Explain Different Security and Integrity Threats to the Database
Database security is the business of the entire organization as all people use the data held in the organizations database and any loss or corruption to data would affect the. Although the security program cannot improve the accuracy of the data that is put into the system by users.

Software Defined Security Cloudpassage Cloud Services Cloud Computing Risk Management
Its worth noting that the security solutions can target multiple threats so dont limit yourself to trying one of them if you suspect a single culprit such as a virus.

. Given below are some database security threats. Data security is one of the measures used to maintain data integrity as unauthorized access to sensitive data can lead to changing records and data loss. Backup and recovery procedures.
Threat to a database may be intentional or accidental. Protecting data against external factors such as natural calamities power outages or hackers falls under the domain of physical integrity. The threats identified over the last couple of years are the same that continue to plague businesses today according to Gerhart.
Loss of availability of data. The challenges of the security program are to ensure that data is maintained in the state that is expected by the users. Data tampering Eavesdropping and data theft.
Loss of confidentiality or secrecy. Data security is not the same as data integrity. Data security is necessary to ensure that no one can access or change the information without authorization while data integrity means that its accurate.
Threat can be anything that can take advantage of a vulnerability to breach security and negatively alter erase harm object or objects of interest. Human error transfer errors bugs and viruses hacking cyber-threats compromised hardware and physical compromise to devices. DATABASE THREATS Since database contains vital information therefore it also faces a lots of threats.
Integrity is the protection of system data from international or accidental unauthorized changes. Outsider or external threats are those that come from outside of the organization and usually are carried out by hacktivists other countries and even competition. Data integrity is not to be confused with data security.
Loss of data integrity. Some security controls designed to maintain the integrity of information include. Moreover human faults storage attrition and several other problems can make it unmanageable for data operators to obtain information from a database.
Entity Integrity - This is related to the concept of primary keys. Data integrity is essential for businesses. Database security must address and protect the following.
Database security refers to the process of protects and safeguards the database from unauthorized access or cyber-attacks. Weve come a long way from Elk Cloner the 1982 Apple virus created by a secondary. THREATS to security and integrity A threat is any situation event or personnel that will adversely effect the database security and smooth and efficient functioning of the organization.
There are different types of database security such as encryption authentication backup application security and physical security which should implement in your business. The threats can be categorized as follows. Common methods include ransomware phishing attacks and hacking.
Database Management system is not safe from intrusion corruption or destruction by people who. Top Database Threats. Data integrity is enforced using the following three integrity constraints.
This article will focus primarily on confidentiality since its the element thats compromised in most data breaches. These listed circumstances mostly signify the areas in which the organization should focus on reducing the risk that is the chance of incurring loss or damage to data within a database. Data integrity in the database is the correctness consistency and completeness of data.
Data security threats can be divided into insider and outsider threats. Database security refers to the range of tools controls and measures designed to establish and preserve database confidentiality integrity and availability. Database security begins with physical security for the systems that host the database management system DBMS.
Database security is the protection of the database against intentional and unintentional threats that may be computer -based or non- computer -based. Database security programs are designed to protect not only the data within the database but also the data management system itself and every application that accesses it from misuse. Data integrity refers to whether or not there are errors in your data like if its valid and accurate.
Credential Threats Employing substandard password management and authentication methods can allow identity theft brute force attacks and social engineering schemes such as phishing. Loss of data privacy. Data integrity can be compromised several ways.
For example in a data breach that compromises integrity a hacker may seize data and modify it before sending it on to the intended recipient. Forgotten databases or new ones that the security team does not know about can be a serious database security and integrity threat. If users are granted database privileges that exceed their use or requirements then these privileges can be used to gain some confidential information.
Here are 10 data threats and how to build up your defences around them. Database security includes a variety of measures used to secure database management systems from malicious cyber-attacks and illegitimate use. All tables should have their own primary keys which should uniquely identify a row and not be NULL.
What is Database Security. Data security focuses on how to minimize the risk of leaking intellectual property business documents healthcare data emails trade secrets and more. Information Security threats can be many like Software attacks theft of intellectual property identity theft theft of equipment or information sabotage and information extortion.
Importance of Security in Database Environment. Data security refers to the protection of data while data integrity refers to the trustworthiness of data. The most common database threats include.

Pdf Database Security Threats Prevention

The Overview Of Database Security Threats Solutions Traditional And Machine Learning

What Are The Roles And Responsibilities Of Automation Tester Soft Skills Problem Solving Skills Effective Communication

Rest Api Security Vulnerabilities Dzone Encryption Algorithms Vulnerability Security

Learn What Are The Most Important Api Security Threats Engineering Leaders Should Be Aware Of And Steps You Can Take To Prevent The Security Threat Ddos Attack

Database Security All You Need To Know In 5 Easy Points Jigsaw Academy

Pdf Database Security Attacks And Control Methods

8 Critical Database Security Best Practices To Keep Your Data Safe
What Is A Security Threat Debricked
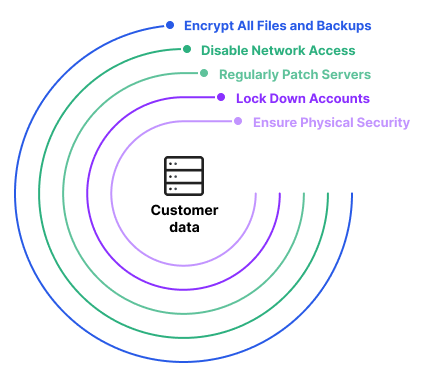
What Is Database Security Threats Best Practices Imperva

Api Architecture Cheatsheet In 2022

What Is Database Security Definition From Techopedia
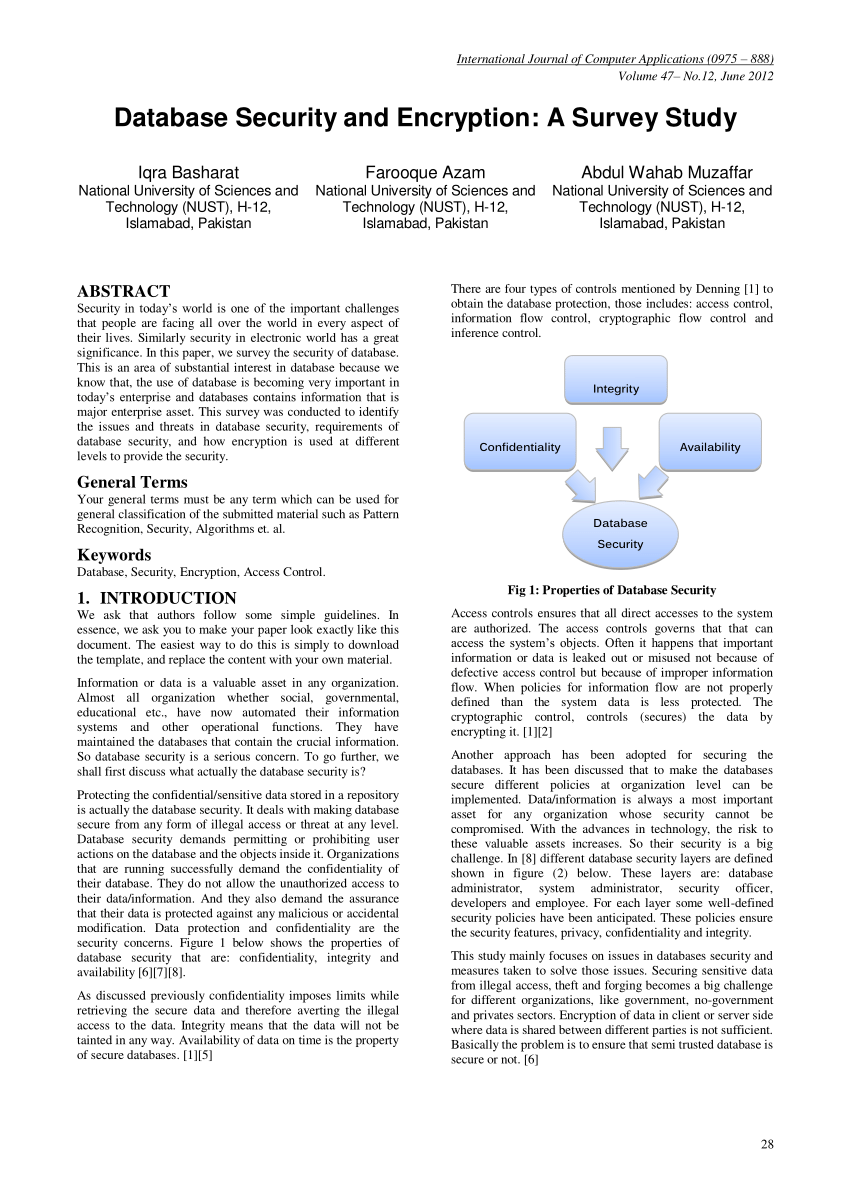
Pdf Database Security And Encryption A Survey Study

Pdf Security Issues In Databases
Pdf A Survey Of Mobile Database Security Threats And Solutions For It

The Pillars Of Information Security Senhasegura

Database Security Databasse Security Control Tools And Benefits

Moving To The Cloud Maximizing Vmware Investment With Dell Emc Data Protection Data Protection Cloud Infrastructure Public Cloud

Comments
Post a Comment